Automating Windows Server Environment Updates With Ansible
Hello Everyone, Nowadays, automating IT environments is one of the biggest challenges for IT Administrators and these tasks brings more…

Hello Everyone, Nowadays, automating IT environments is one of the biggest challenges for IT Administrators and these tasks brings more…
Hello Blog! Today I’m gonna explain Powershell arrays, which is the most important part of the scripting and coding in…
Windows Deployment Services is a technology for deploying Windows on multiple computers without using CD/DVD on each computer. If you…
![Windows Quick Access Shortcut Commands [ My TechNet Wiki Post ]](https://hamidsadeghpour.net/wp-content/uploads/2019/03/TechNet.jpg)
Access Windows Servcies with MSC Commands. Hello Wiki, sometimes I see some experts follow GUI pathes in order to access…

Sconfig comes from Server Configuration from Command prompt like CMD or Windows Powershell. In Windows Server Core Edition the only…
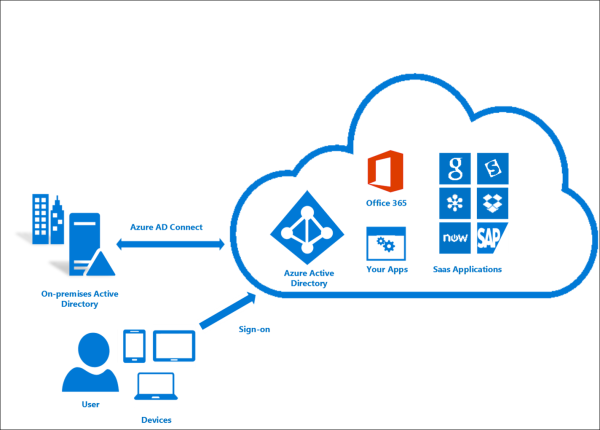
Azure Active Directory (Azure AD) is Microsoft’s cloud-based identity and access management service. Azure AD helps your employees sign in…
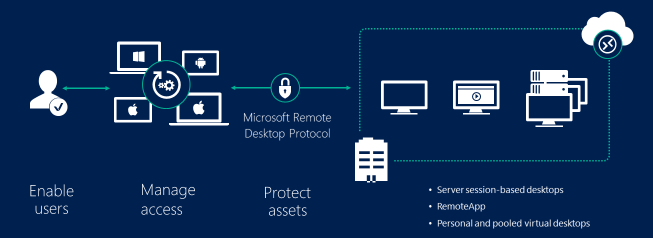

I thought to clean up and re-publish my blog on AD ports requirements. Yes, they are extensive, to the dismay…
![Microsoft Active Directory Certificate Services [AD CS] Installation](https://hamidsadeghpour.net/wp-content/uploads/2019/03/CA-Srv-768x432.jpg)
Microsoft Active Directory Certificate Services [AD CS] provides a platform for issuing and managing public key infrastructure [PKI] certificates. On top of…

In the series of posts this month we’ve been looking at network ports relevant to security administrators. This note explores…

DHCP is used to dynamically assign IP addresses to client machines. This tutorial is written to help you to install…

Windows Deployment Services (WDS) is a really interesting tool from Microsoft. It allows an administrator to remotely deploy Windows operating systems to machines booting…