Microsoft Azure: ExpressRoute Capabilities
Hello Blog, Today we’re gonna go over Microsoft Azure ExpressRoute Capabilities with some more detail and the benefits which can…
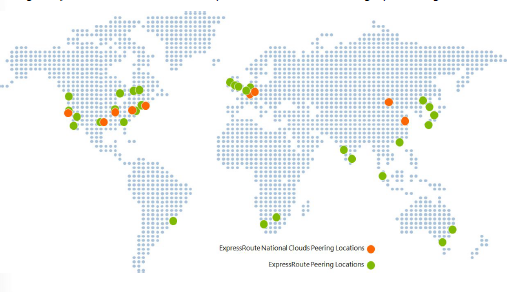
Hello Blog, Today we’re gonna go over Microsoft Azure ExpressRoute Capabilities with some more detail and the benefits which can…
![Bootcamp [Event] Microsoft Azure Migration Service](https://hamidsadeghpour.net/wp-content/uploads/2020/08/Hamid-2-Azure-Migration-Service-768x761.png)
Hello Blog, Delighted to announce that I’m having an online talk with Microsoft Learn Student Ambassadors and The University of…
![Bootcamp [Event] Microsoft Azure Cloud in General](https://hamidsadeghpour.net/wp-content/uploads/2020/08/Hamid-1-Azure-Cloud-in-General-768x761.png)
Hello Blog, Delighted to announce that I’m having an online talk with Microsoft Learn Student Ambassadors and The University of…

Hello Blog, Here I am again, this time wanna write a short article about the strategies that we are able…
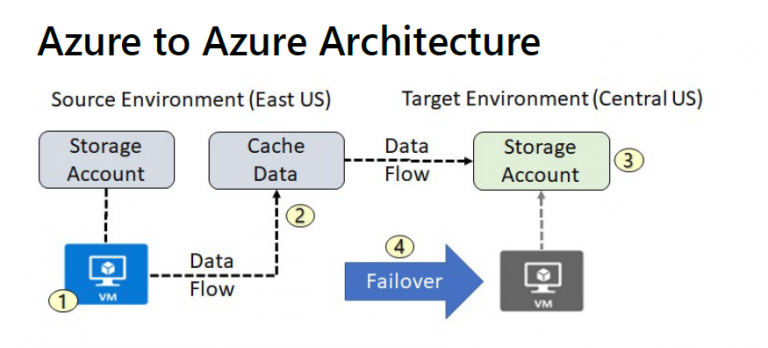
When you enable replication for an Azure VM, the following happens: 1. The Site Recovery Mobility service extension is automatically…

Azure Backup Azure Backup is the Azure-based service you can use to back up (or protect) and restore your data…
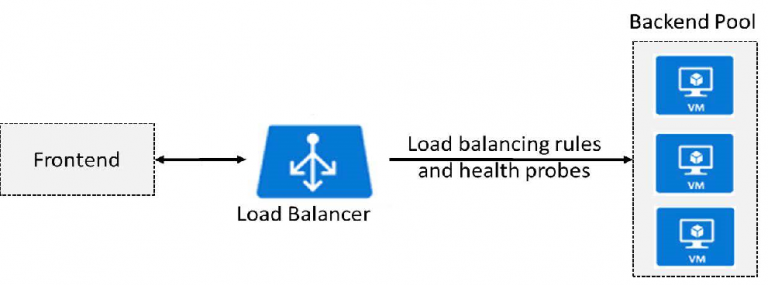
Azure Load Balancer: ( from AZ-103 Trainer Book ) The Azure Load Balancer delivers high availability and network performance to…

Hello blog! Hope everyone is fine, Today I’m going to share my PPT file which is a Microsoft Azure Migrate…

Hello Blog, As you know and familiar with Azure Compute Services specifically Azure Virtual Machines which is one of the…
Check PowerShell CLub Now for new PowerShell Script! Thank you Club! http://www.powershellclub.com/viewtopic.php?f=13&p=98#p98
![Public Cloud and Private Cloud Differences [ Microsoft Azure ]](https://hamidsadeghpour.net/wp-content/uploads/2019/12/azure.png)
Hello Everyone, In this article I am going to write about the differences between Public Cloud with examples of some…

Hello everyone, Pleased to share with everyone, after years of works and community contributions with my heart I got the…